项目部署笔记
针对没有外网的服务器
注意
- 当前系统和服务器系统需要有docker环境,且版本大于20
- 由于服务器无法联网,相关docker镜像需要自己想办法弄进去
- 如果使用方法一部署前端,则需要自己弄镜像,如果使用方法二部署前端,服务器需要安装了nginx且配置完毕
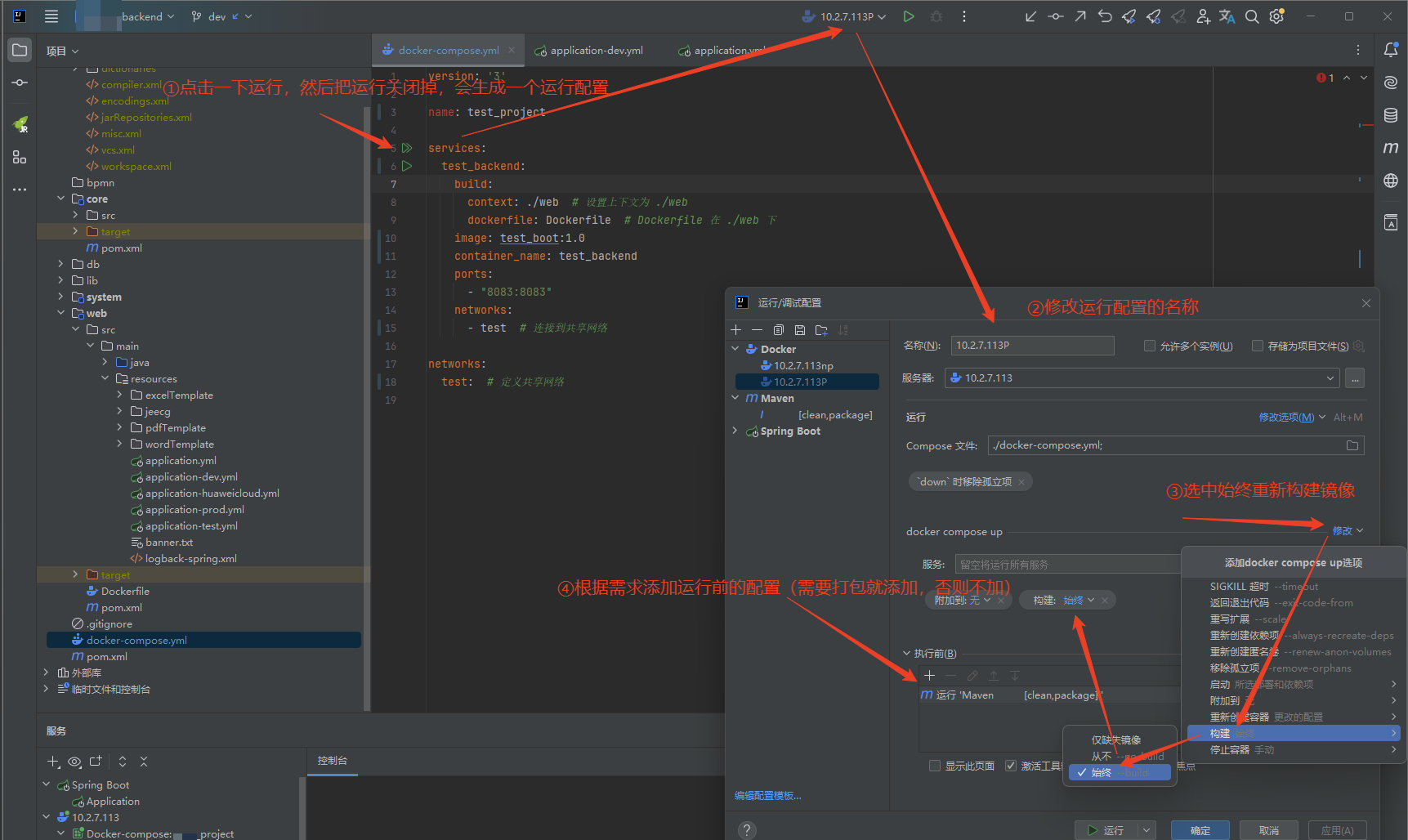
采用idea或webstorm进行部署
下方需要替换的关键词:证书、域名、项目
后端
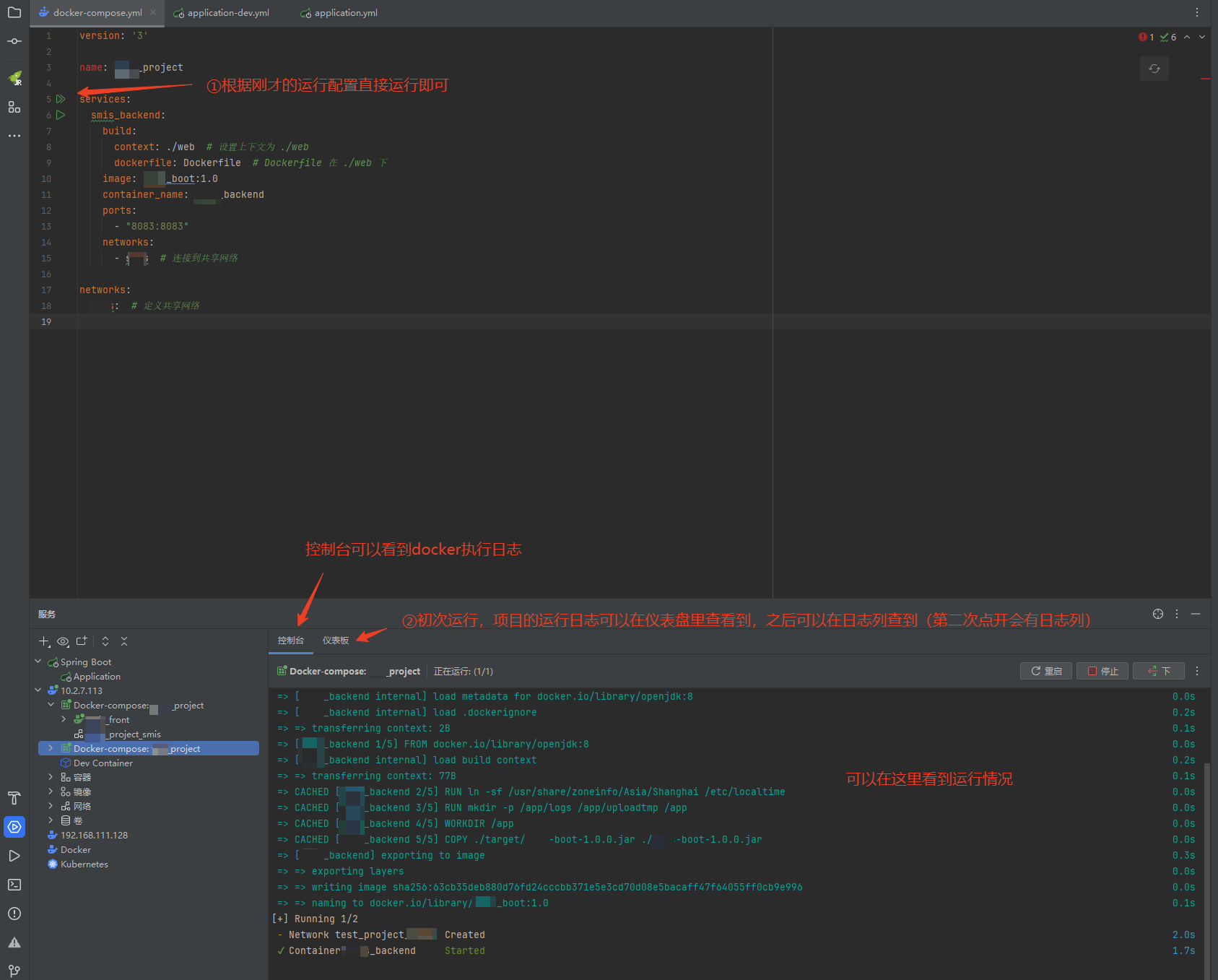
部署方式为:idea+dockerfile+dockercompose
dockerfile例子
dockerfile
# 使用OpenJDK 作为基础镜像
FROM openjdk:8
# 作者信息
LABEL maintainer="bzl"
# 设置时区
RUN ln -sf /usr/share/zoneinfo/Asia/Shanghai /etc/localtime
# 创建必要的目录
RUN mkdir -p /app/logs /app/uploadtmp /app
# 设置工作目录
WORKDIR /app
# 将构建的 jar 文件添加到容器中
COPY ./target/test-boot-1.0.0.jar ./test-boot-1.0.0.jar
# 暴露应用的端口
EXPOSE 8083
# 设置容器启动时执行的命令(此处强制使用prod的配置文件)
CMD ["java", "-Djava.io.tmpdir=/app/uploadtmp", "-Duser.timezone=GMT+08", "-Dspring.profiles.active=prod", "-jar", "test-boot-1.0.0.jar"]docker-compose例子
yaml
version: '3'
name: test_project
services:
test_backend:
build:
context: ./web # 设置上下文为 ./web
dockerfile: Dockerfile # Dockerfile 在 ./web 下
image: test_boot:1.0
container_name: test_backend
ports:
- "8083:8083"
networks:
- test # 连接到共享网络
networks:
test: # 定义共享网络部署 生成打包配置文件
生成docker运行配置并配置每次都重新构建镜像
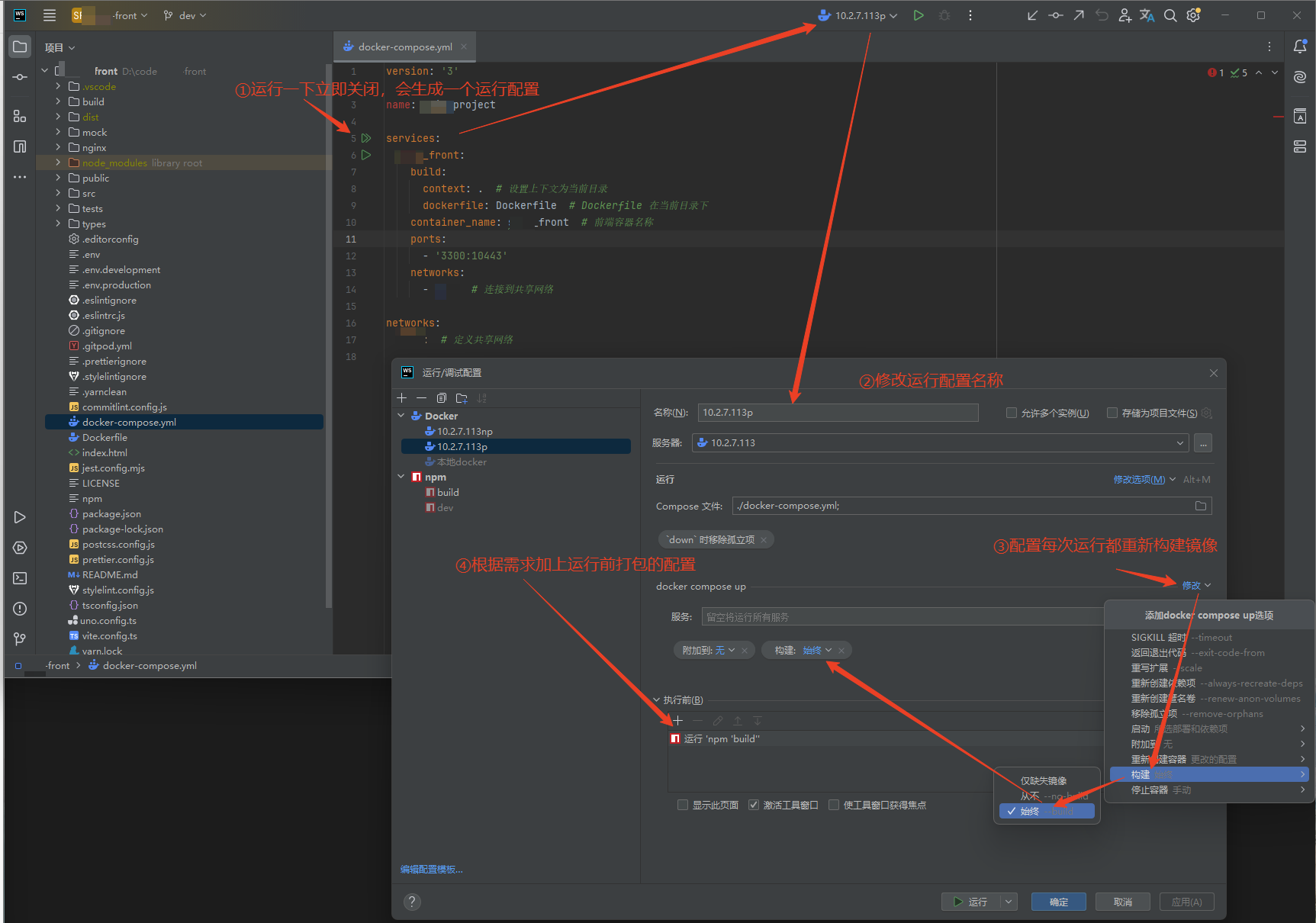
前端
方法一(推荐)
部署方式为:websotrm+dockercompose+dockerfile
准备nginx配置文件和dockersfile(由于win无法和服务器建立数据卷,所以此处需要用dockerfile将需要的文件放到镜像里)
修改运行配置之后运行即可
nginx 相关配置文件
nginx.conf
nginx
user root;
worker_processes 1;
error_log /var/log/nginx/error.log; #日志存放位置
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 1024;
accept_mutex on; multi_accept on; use epoll;}
http {
include mime.types;
default_type application/octet-stream;
#上传文件大小限制
client_max_body_size 15m;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
server_tokens off; # 配置ip限制策略
#include blockip.conf;
fastcgi_intercept_errors on;
proxy_intercept_errors on;
# 限流limit_req_zone,定义一个名为req_zone的共享内存,设置键的大小为10k,并限制请求频率为10次/s
limit_req_zone $binary_remote_addr zone=req_zone:15m rate=10r/s;
#Nginx will not add the port in the url when the request is redirected port_in_redirect off;
port_in_redirect off;
sendfile on; tcp_nopush on; tcp_nodelay on;
client_header_timeout 60;
client_body_timeout 60;
send_timeout 60;
#keepalive_timeout 0;
keepalive_timeout 65;
include gzip.conf;
server {
listen 10443 ssl;
# 1.25.1版本之后,需按照如下格式配置http2
http2 on;
server_name 你证书对应的域名;
client_max_body_size 500m;
large_client_header_buffers 4 1m;
include ssl.conf;
error_page 304 /404.html;
error_page 404 403 400 /404.html;
error_page 500 502 503 504 /505.html;
#access_log logs/host.access.log main;
include header.conf;
include proxy.conf;
include blockip.conf;
include blockip_group.conf;
deny 172.233.243.122;
root /usr/share/nginx/html;
include location.conf;
}
}gzip.conf
nginx
gzip on;
gzip_min_length 1k;
gzip_comp_level 5;
gzip_types text/plain application/javascript application/x-javascript text/css application/xml text/javascript application/x-httpd-php image/jpeg image/gif image/png;
gzip_vary on;
gzip_disable "MSIE [1-6]\.";
gzip_static on;ssl.conf
nginx
ssl_certificate ssl/证书.com.crt;
ssl_certificate_key ssl/证书_RSA.key;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1.2;
#ssl_ciphers HIGH:!aNULL:!MD5;
ssl_ciphers 'ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES256-SHA:HIGH:!MEDIUM:!LOW:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4:@STRENGTH';header.conf
nginx
add_header Content-Security-Policy "default-src *;style-src 'self' 'unsafe-inline';script-src 'self' 'unsafe-inline' 'unsafe-eval';img-src * 'self' blob: https: data:;worker-src * blob:;font-src 'self' data:;";
add_header X-Frame-Options "SAMEORIGIN";
add_header X-XSS-Protection "1; mode=block";
add_header Strict-Transport-Security "max-age=31536000";
add_header Referrer-Policy "strict-origin-when-cross-origin";
add_header X-Download-Options noopen;
add_header X-Content-Type-Options nosniff;
add_header X-Permitted-Cross-Domain-Policies value;
add_header Access-Control-Allow-Origin "https://域名:3300";
add_header Access-Control-Allow-Headers "Origin, X-Requested-With, Content-Type, Accept";proxy.conf
nginx
proxy_connect_timeout 500ms;
proxy_send_timeout 1000ms;
proxy_read_timeout 50000ms;
proxy_buffers 64 8k;
proxy_busy_buffers_size 128k;
proxy_temp_file_write_size 64k;
proxy_redirect off;
proxy_next_upstream error invalid_header timeout http_502 http_504;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Real-Port $remote_port;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_hide_header X-Powered-By;location.conf
nginx
location ~* \s(\.(svn|git|sql|bak|old|tar|gz|tgz|zip|7z|rar|DS_store)$) {
deny all;
}
include nginx_deny_url.conf;
location ^~ /filePreviewer {
proxy_pass http://10.2.7.113:8012/onlinePreview;
set $Real $proxy_add_x_forwarded_for;
if ( $Real ~ (\d+)\.(\d+)\.(\d+)\.(\d+),(.*) ) {
set $Real $1.$2.$3.$4;
}
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
real_ip_header X-Forwarded-For;
real_ip_recursive on; proxy_cookie_path / "/项目名-boot; Secure; HttpOnly; ";
proxy_read_timeout 300;
proxy_send_timeout 300;
}
location ^~ /项目名-boot/ {
proxy_pass http://容器名称:8083/项目名-boot/;
set $Real $proxy_add_x_forwarded_for;
if ( $Real ~ (\d+)\.(\d+)\.(\d+)\.(\d+),(.*) ) {
set $Real $1.$2.$3.$4;
}
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
real_ip_header X-Forwarded-For;
real_ip_recursive on; proxy_cookie_path / "/项目名-boot; Secure; HttpOnly; ";
}
location / {
# alias /data/项目名/front/;
# index index.html; # try_files $uri $uri/ /front/index.html; proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
proxy_set_header X-NginX-Proxy true;
limit_except GET POST HEAD {
deny all;
}
try_files $uri $uri/ /index.html;
}nginx_deny_url.conf
这个文件用于防止攻击者访问以下路径(根据nginx的error日志进行整理)
nginx
#location ~* /../{
# deny all;
#}
location ~* /..\;/{
deny all;
}
location ~* /\;/{
deny all;
}
location ^~ /druid {
deny all;
}
location ^~ /actuator {
deny all;
}
location ^~ /gateway/ {
deny all;
}
location ^~ /nacos/ {
deny all;
}
location ^~ /swagger-ui.html {
deny all;
}
location ^~ /swagger {
deny all;
}
location ^~ /webjars/ {
deny all;
}
location ^~ /v2/api-docs/ {
deny all;
}
location ^~ /jmreport/ {
deny all;
}
location ^~ /console/ {
deny all;
}
location ^~ /etc/ {
deny all;
}
location ^~ /cgi-bin/ {
deny all;
}
location ~* /tenant/ {
deny all;
}
location ~* /sysUserAgent/ {
deny all;
}
location ~* /thirdLogin/ {
deny all;
}
location ~* /thirdApp/ {
deny all;
}
location ~* /ng-alain/{
deny all;
}
location ^~ /项目名-boot/camunda/app/{
deny all;
}
location ^~ /manage/{
deny all;
}
location ~* /env\;.js{
deny all;
}
location ^~ /filePreviewer/index {
deny all;
}
location ^~ /filePreviewer/getCorsFile {
deny all;
}
location ^~ /filePreviewer/fileUpload {
deny all;
}
location ~* /swagger-resources/ {
deny all;
}
location ~* /swagger/ {
deny all;
}
location ~* /cgi/ {
deny all;
}
location ~* /vpn/ {
deny all;
}
location ~* /root/ {
deny all;
}
location ~* /admin/ {
deny all;
}
location ~* /WEB-INF/ {
deny all;
}
location ~* /AccessAnywhere/ {
deny all;
}
location ~* /online/ {
deny all;
}
location ~* /druid/ {
deny all;
}blockip_group.conf和blockip.conf
这个两文件主要列出了一些用于禁用的ip,例如下述两个攻击我服务器的ip,其他不方便透露
nginx
deny 172.12.62.0/24;
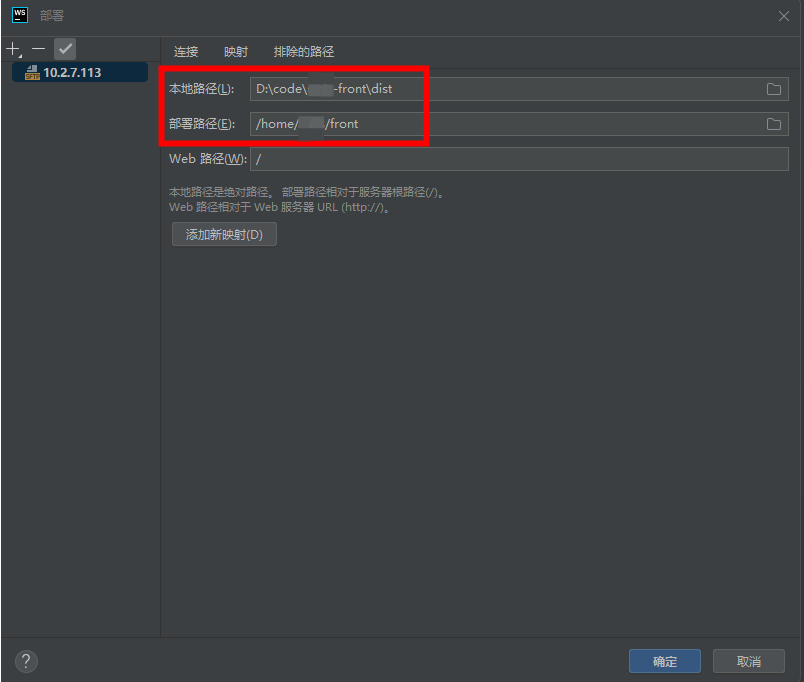
deny 101.200.138.178;方法二
部署方式为:webstorm+sftp